Let's Encrypt CA Root Hierarchy Chain Evolution History

2015: Let’s Encrypt Root CA Initial Setup
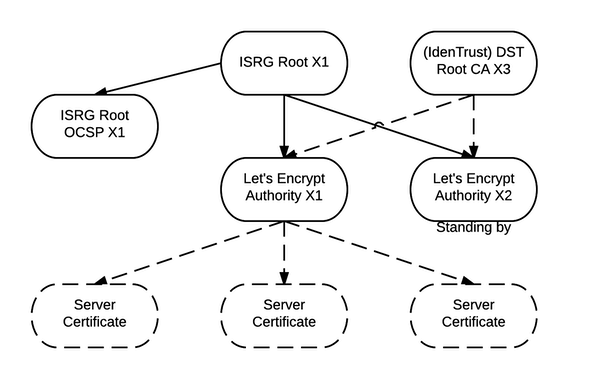
In 2015, Let’s Encrypt have three CA certificates:
- ISRG Root X1 Certificate
- Let’s Encrypt Intermediate X1 CA Certificate
- Let’s Encrypt Intermediate X2 CA Certificate
Let’s Encrypt will issue certificates to subscribers from its intermediate CAs, allowing Let’s Encrypt to keep root CA safely offline. IdenTrust will cross-sign Let’s Encrypt intermediates. This allow our end certificates to be accepted by all major browsers while Let’s Encrypt propagate its own root.
The private keys for the ISRG root CA and the Let’s Encrypt intermediate CAs are stored on hardware security modules (HSMs), which provide a high degree of protection against the keys being stolen.
Before 2020 September: Cross signed by IdenTrust’s DST Root CA X3
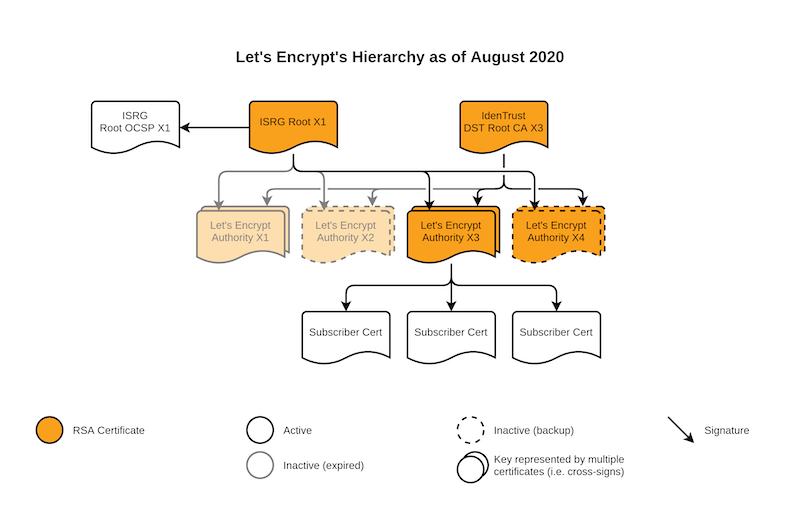
One root: the ISRG Root X1, which has a 4096-bit RSA key and is valid until 2035.
4 intermediate CA: the Let’s Encrypt Authorities X1, X2, X3, and X4. The first two were issued when Let’s Encrypt first began operations in 2015, and were valid for 5 years. The latter two were issued about a year later, in 2016, and are also valid for 5 years, expiring about this time next year. All of these intermediates use 2048-bit RSA keys. In addition, all of these intermediates are cross-signed by IdenTrust’s DST Root CA X3, another root certificate controlled by a different certificate authority which is trusted by most root stores.
After 2020 September: ISRG Root X1 as root
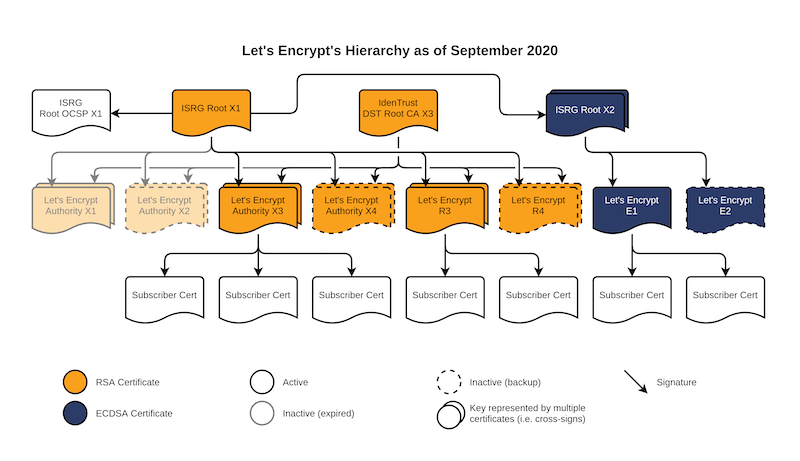
Now that ISRG Root X1 root CA is widely trusted by browsers, Letsencrypt transition using ISRG Root X1 root CA directly, without a cross-sign.
New ISRG Root X2, which has an ECDSA P-384 key instead of RSA, and is valid until 2040. Issued from that, we have two new intermediates, E1 and E2, which are both also ECDSA and are valid for 5 years.
The ISRG Root X2 itself is cross-signed by our existing ISRG Root X1
2020 December: Extending Android Device Compatibility
ISRG Root X1 is not widely trusted by Android device, especially on Android operating systems prior to 7.1.1.
Extending Android Device Compatibility by cross-sign for ISRG Root X1 from DST Root CA X3.
2021 August: Up to date Let’s Encrypt CA trust chain.
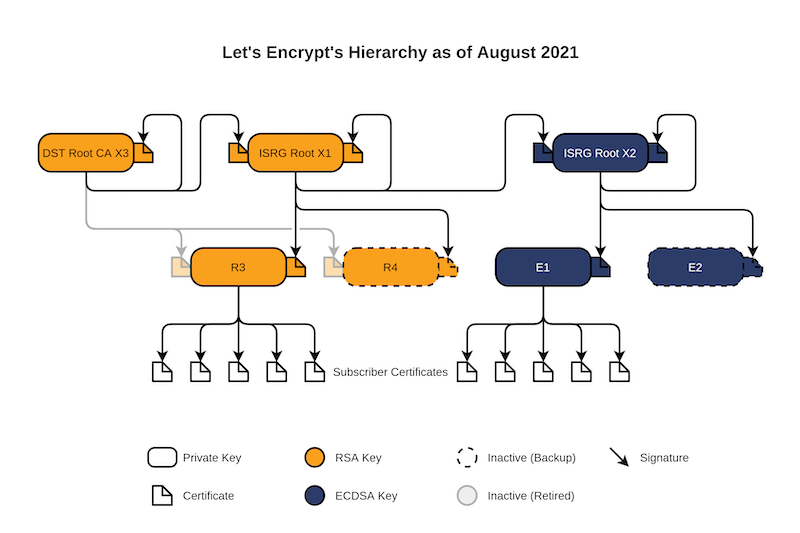
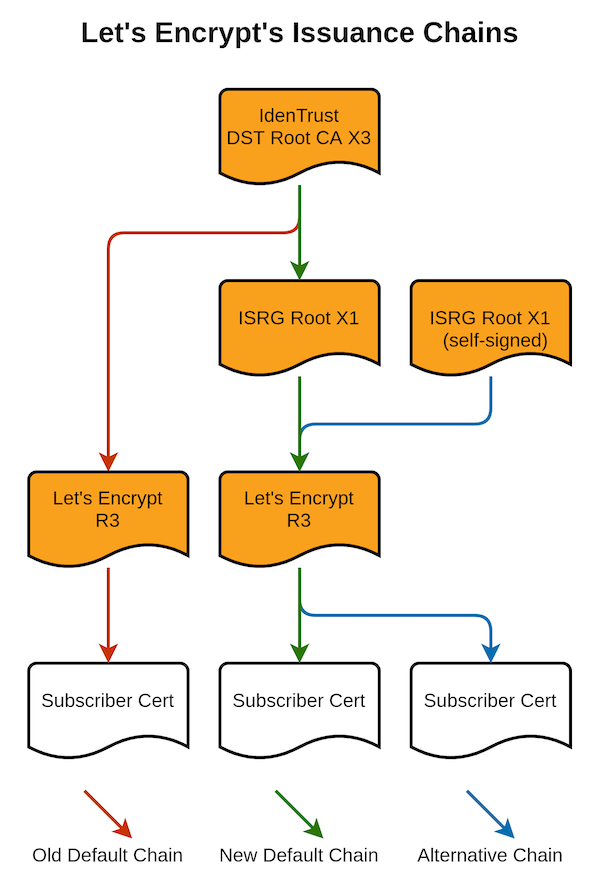
This is the current up to date Let’s Encrypt CA trust chain.
ISRG Root X2 was generated in fall 2020 and is the root certificate for the ECDSA hierarchy. It is represented by two certificates: one that is self-signed and one that is signed by ISRG Root X1.
All certificates signed by the ECDSA intermediate “E1” will come with a chain including an intermediate certificate whose Subject is “ISRG Root X2” and whose Issuer is “ISRG Root X1”. Almost all server operators will choose to serve this chain as it offers the most compatibility until ISRG Root X2 is widely trusted.
Related pages:
- Detailed Explanation of PKI Terminology and Definitions
- Online X509 Certificate Viewer / Decoder
- Certificate Revoke: Certificate Revocation List (CRL) Structure File Format and OpenSSL CRL Examples Decode CRL
- Certificate Revoke: Online Certificate Status Protocol (OCSP) With Example Request/Response
References
- https://letsencrypt.org/certificates/
- https://letsencrypt.org/docs/dst-root-ca-x3-expiration-september-2021/
- https://letsencrypt.org/2020/12/21/extending-android-compatibility.html
- https://letsencrypt.org/2020/09/17/new-root-and-intermediates.html
- https://letsencrypt.org/2019/04/15/transitioning-to-isrg-root.html
- https://letsencrypt.org/2015/06/04/isrg-ca-certs.html
- Let’s Encrypt ISRG Root X1 Certificate
- Let’s Encrypt ISRG Root X2 Certificate
- Let’s Encrypt R3 Certificate