Certificate Revoke: Online Certificate Status Protocol (OCSP) With Example Request/Response
OCSP Introduction
The Online Certificate Status Protocol ( OCSP) is documented in the RFC 6960: X.509 Internet Public Key Infrastructure Online Certificate Status Protocol.
OCSP is a relatively simple request/response protocol useful in determining the current status of a digital certificate without requiring CRLs.
OCSP encoded in ASN.1.
OCSP Request
An OCSP request contains the following data:
- protocol version (currently only Version 1 is defined).
- service request.
- one or more target certificate identifier. The certificate identifier consists of the hash of the certificate issuer’s DN, the hash of the issuer’s public key, and the certificate serial number.
- optional extensions, which MAY be processed by the OCSP responder.
OCSP request ASN.1 structure:
OCSPRequest ::= SEQUENCE {
tbsRequest TBSRequest,
optionalSignature [0] EXPLICIT Signature OPTIONAL }
TBSRequest ::= SEQUENCE {
version [0] EXPLICIT Version DEFAULT v1,
requestorName [1] EXPLICIT GeneralName OPTIONAL,
requestList SEQUENCE OF Request,
requestExtensions [2] EXPLICIT Extensions OPTIONAL }
Signature ::= SEQUENCE {
signatureAlgorithm AlgorithmIdentifier,
signature BIT STRING,
certs [0] EXPLICIT SEQUENCE OF Certificate OPTIONAL}
Version ::= INTEGER { v1(0) }
Request ::= SEQUENCE {
reqCert CertID,
singleRequestExtensions [0] EXPLICIT Extensions OPTIONAL }
CertID ::= SEQUENCE {
hashAlgorithm AlgorithmIdentifier,
issuerNameHash OCTET STRING, -- Hash of issuer's DN
issuerKeyHash OCTET STRING, -- Hash of issuer's public key
serialNumber CertificateSerialNumber }
OCSP Response
The basic response type contains:
- the version of the response syntax, which MUST be v1 (value is 0) for this version of the basic response syntax;
- either the name of the responder or a hash of the responder’s public key as the ResponderID;
- the time at which the response was generated;
- certificate status responses for each of the certificates in a request;
goodrevokedIf the status of a given certificate isrevokedthe time that the revocation occurred is indicated and, optionally, the reason for revocation may also be included.unknown
- optional extensions;
- a signature computed across a hash of the response; and
- the signature algorithm OID.
Note
The OCSP responses must be digitally signed to provide assurance that the response is originating with a trusted entity and that it is not altered in transit.OCSP response ASN.1 structure:
OCSPResponse ::= SEQUENCE {
responseStatus OCSPResponseStatus,
responseBytes [0] EXPLICIT ResponseBytes OPTIONAL }
OCSPResponseStatus ::= ENUMERATED {
successful (0), -- Response has valid confirmations
malformedRequest (1), -- Illegal confirmation request
internalError (2), -- Internal error in issuer
tryLater (3), -- Try again later
-- (4) is not used
sigRequired (5), -- Must sign the request
unauthorized (6) -- Request unauthorized
}
OCSP Request/Response Example with OpenSSL
OpenSSL ocsp is utility can perform OCSP request and response:
The
openssl ocspcommand performs many common OCSP tasks. It can be used to print out requests and responses, create requests and send queries to an OCSP responder and behave like a mini OCSP server itself.
Useful OCSP Client Options:
-help
Print out a usage message.
-out filename
specify output filename, default is standard output.
-issuer filename
This specifies the current issuer certificate. This option can be used multiple times. The certificate specified in filename must be in PEM format. This option MUST come before any -cert options.
-cert filename
Add the certificate filename to the request. The issuer certificate is taken from the previous issuer option, or an error occurs if no issuer certificate is specified.
-req_text, -resp_text, -text
Print out the text form of the OCSP request, response or both respectively.
-reqout file, -respout file
Write out the DER encoded certificate request or response to file.
-reqin file, -respin file
Read OCSP request or response file from file. These option are ignored if OCSP request or response creation is implied by other options (for example with serial, cert and host options).
-url responder_url
Specify the responder URL. Both HTTP and HTTPS (SSL/TLS) URLs can be specified.
Let’s use www.example.com certificate as an example.
The certificate info OCSP url and issuer.
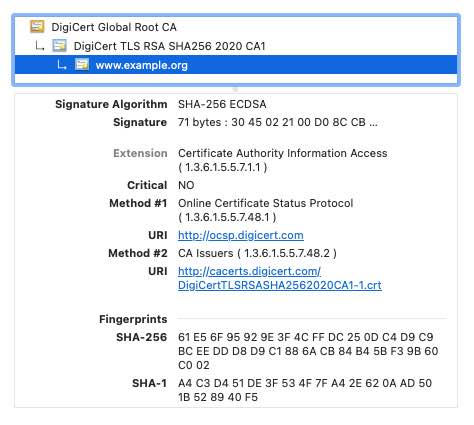
Get Server Certificate Example
First we need get www.example.com’s server public certificate, you can use openssl s_client
command to dump server certificate:
$ echo -n | openssl s_client -connect www.example.com:443 | \
sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p' > cert.pem
Create OCSP Request Example
Create an OCSP request and write it to a file in DER format, then parse the file content with asn1parse:
The
openssl asn1parsecommand is a diagnostic utility that can parse ASN.1 structures. It can also be used to extract data from ASN.1 formatted data.
$ openssl ocsp -issuer issuer.crt -cert cert.pem -reqout req.der
$ openssl asn1parse -in req.der -inform der
0:d=0 hl=2 l= 118 cons: SEQUENCE
2:d=1 hl=2 l= 116 cons: SEQUENCE
4:d=2 hl=2 l= 77 cons: SEQUENCE
6:d=3 hl=2 l= 75 cons: SEQUENCE
8:d=4 hl=2 l= 73 cons: SEQUENCE
10:d=5 hl=2 l= 9 cons: SEQUENCE
12:d=6 hl=2 l= 5 prim: OBJECT :sha1
19:d=6 hl=2 l= 0 prim: NULL
21:d=5 hl=2 l= 20 prim: OCTET STRING [HEX DUMP]:E4E395A229D3D4C1C31FF0980C0B4EC0098AABD8
43:d=5 hl=2 l= 20 prim: OCTET STRING [HEX DUMP]:B76BA2EAA8AA848C79EAB4DA0F98B2C59576B9F4
65:d=5 hl=2 l= 16 prim: INTEGER :025216E1C4998E2632AA5D1DA985B43C
83:d=2 hl=2 l= 35 cons: cont [ 2 ]
85:d=3 hl=2 l= 33 cons: SEQUENCE
87:d=4 hl=2 l= 31 cons: SEQUENCE
89:d=5 hl=2 l= 9 prim: OBJECT :OCSP Nonce
100:d=5 hl=2 l= 18 prim: OCTET STRING [HEX DUMP]:0410362377E3EF4F658AA5018494EC29F735
Send OCSP Request to OCSP Server Example
Send a query to an OCSP responder with URL http://ocsp.digicert.com/ save the response to a file, print it out in text form, and verify the response:
$ openssl ocsp -issuer issuer.pem -cert cert.pem \
-url http://ocsp.digicert.com -resp_text -respout resp.der
OCSP Response Data:
OCSP Response Status: successful (0x0)
Response Type: Basic OCSP Response
Version: 1 (0x0)
Responder Id: B76BA2EAA8AA848C79EAB4DA0F98B2C59576B9F4
Produced At: Feb 18 09:06:24 2022 GMT
Responses:
Certificate ID:
Hash Algorithm: sha1
Issuer Name Hash: E4E395A229D3D4C1C31FF0980C0B4EC0098AABD8
Issuer Key Hash: B76BA2EAA8AA848C79EAB4DA0F98B2C59576B9F4
Serial Number: 025216E1C4998E2632AA5D1DA985B43C
Cert Status: good
This Update: Feb 18 08:51:00 2022 GMT
Next Update: Feb 25 08:06:00 2022 GMT
Signature Algorithm: sha256WithRSAEncryption
2f:b4:df:fe:bf:ed:e9:a8:79:73:30:b7:be:e3:ca:07:3b:8f:
c6:15:3a:fd:ab:77:99:04:13:19:8b:4a:eb:2c:93:73:46:86:
f3:6d:ff:ee:60:2f:f8:f6:4e:bb:5d:c8:76:41:ec:91:af:b4:
51:d0:88:c5:e8:07:c5:4f:ca:e5:25:91:b4:c4:64:ab:70:5b:
ea:e0:9d:ae:1c:16:76:39:6d:a4:38:51:81:cb:fa:9c:3b:7f:
8b:b6:34:3f:5c:34:3d:0c:b5:38:00:b6:9e:7f:99:e6:5f:1d:
31:82:d2:a8:e4:15:3c:c4:2c:a1:7a:bb:0c:77:3f:e9:dc:5d:
98:de:68:a1:94:fd:6e:e0:7f:12:36:e4:30:08:e2:19:f5:f9:
7e:11:19:49:0b:87:47:d7:a8:14:aa:29:d2:75:8b:0e:3a:25:
c5:75:c5:d2:21:3f:ba:db:4a:fa:f1:12:ef:34:c1:7c:61:88:
de:e2:dd:50:69:14:06:0f:75:c8:a1:12:ee:4b:4e:84:3c:95:
ab:2e:04:1b:65:6f:df:0e:73:1f:a7:b2:cf:ff:1c:49:c7:93:
c3:cc:10:c3:42:d9:4d:cd:37:c3:0b:19:5a:ea:65:05:bf:72:
72:3b:1d:80:3e:9c:ab:8f:04:17:54:7b:8d:19:be:61:e1:2d:
ac:14:4a:c2
cert.pem: good
This Update: Feb 18 08:51:00 2022 GMT
Next Update: Feb 25 08:06:00 2022 GMT
The response includes Certificate ID, Cert Status (in this response the value is good)
Responses:
Certificate ID:
Hash Algorithm: sha1
Issuer Name Hash: E4E395A229D3D4C1C31FF0980C0B4EC0098AABD8
Issuer Key Hash: B76BA2EAA8AA848C79EAB4DA0F98B2C59576B9F4
Serial Number: 025216E1C4998E2632AA5D1DA985B43C
Cert Status: good
This Update: Feb 18 08:51:00 2022 GMT
Next Update: Feb 25 08:06:00 2022 GMT
If there are multiple certificates in request, can use multiple -cert in request, for example:
openssl ocsp -issuer issuer.pem -cert cert.pem -cert cert2.pem \
-url ocsp.digicert.com -resp_text -respout resp.der
Parse OCSP Response Example
Read in an OCSP response and print out text form:
$ openssl ocsp -respin resp.der -text -noverify
OCSP Response Data:
OCSP Response Status: successful (0x0)
Response Type: Basic OCSP Response
Version: 1 (0x0)
Responder Id: B76BA2EAA8AA848C79EAB4DA0F98B2C59576B9F4
Produced At: Feb 18 09:06:24 2022 GMT
Responses:
Certificate ID:
Hash Algorithm: sha1
Issuer Name Hash: E4E395A229D3D4C1C31FF0980C0B4EC0098AABD8
Issuer Key Hash: B76BA2EAA8AA848C79EAB4DA0F98B2C59576B9F4
Serial Number: 025216E1C4998E2632AA5D1DA985B43C
Cert Status: good
This Update: Feb 18 08:51:00 2022 GMT
Next Update: Feb 25 08:06:00 2022 GMT
Signature Algorithm: sha256WithRSAEncryption
2f:b4:df:fe:bf:ed:e9:a8:79:73:30:b7:be:e3:ca:07:3b:8f:
c6:15:3a:fd:ab:77:99:04:13:19:8b:4a:eb:2c:93:73:46:86:
f3:6d:ff:ee:60:2f:f8:f6:4e:bb:5d:c8:76:41:ec:91:af:b4:
51:d0:88:c5:e8:07:c5:4f:ca:e5:25:91:b4:c4:64:ab:70:5b:
ea:e0:9d:ae:1c:16:76:39:6d:a4:38:51:81:cb:fa:9c:3b:7f:
8b:b6:34:3f:5c:34:3d:0c:b5:38:00:b6:9e:7f:99:e6:5f:1d:
31:82:d2:a8:e4:15:3c:c4:2c:a1:7a:bb:0c:77:3f:e9:dc:5d:
98:de:68:a1:94:fd:6e:e0:7f:12:36:e4:30:08:e2:19:f5:f9:
7e:11:19:49:0b:87:47:d7:a8:14:aa:29:d2:75:8b:0e:3a:25:
c5:75:c5:d2:21:3f:ba:db:4a:fa:f1:12:ef:34:c1:7c:61:88:
de:e2:dd:50:69:14:06:0f:75:c8:a1:12:ee:4b:4e:84:3c:95:
ab:2e:04:1b:65:6f:df:0e:73:1f:a7:b2:cf:ff:1c:49:c7:93:
c3:cc:10:c3:42:d9:4d:cd:37:c3:0b:19:5a:ea:65:05:bf:72:
72:3b:1d:80:3e:9c:ab:8f:04:17:54:7b:8d:19:be:61:e1:2d:
ac:14:4a:c2
OCSP Limitations
OCSP makes no claims whatsoever regarding the validity of the certificate other than its revocation status.
The OCSP responder may have latency response regarding the current revocation status of the certificate.
It is inappropriate to simply assume that OCSP automatically offers fresh and up-to-date information even if it is considered to be a “real-time” service.
The responses from an OCSP responder must be digitally signed, and this may result in a significant performance impact.
Related pages:
- Detailed Explanation of PKI Terminology and Definitions
- Online X509 Certificate Viewer / Decoder
- Let's Encrypt CA Root Hierarchy Chain Evolution History
- Certificate Revoke: Certificate Revocation List (CRL) Structure File Format and OpenSSL CRL Examples Decode CRL