Unveiling the FBI's Legitimate Access to Secure Messaging App Content and Metadata
A source about FBI’s Ability to Legally Access Secure Messaging App Content and Metadata from Jan. 2021 FBI Infographic re Lawful Access to Secure Messaging Apps Data on Property of the People indicate FBI have access to some of end to end encryption message apps.
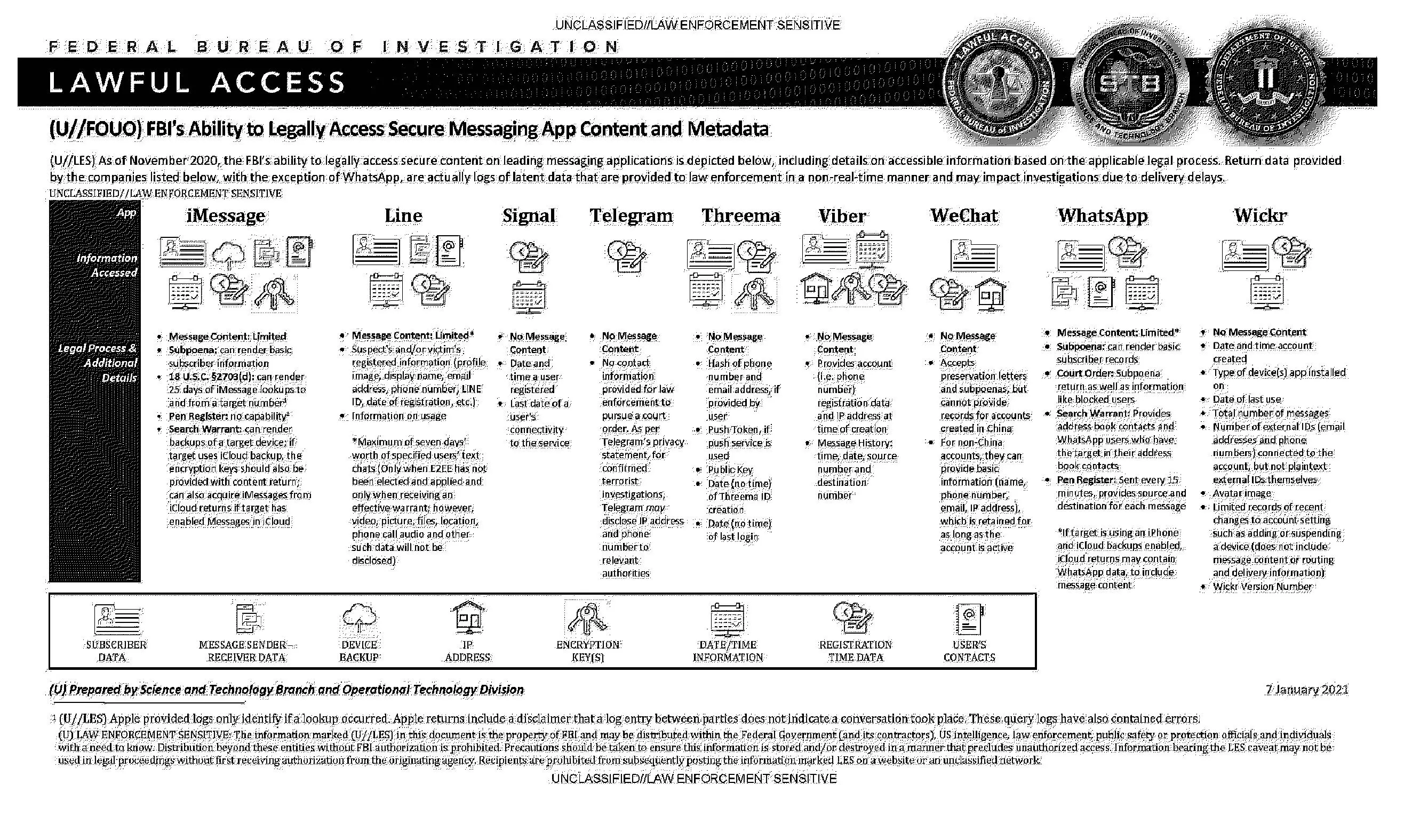
In an era where digital communication has become the norm, ensuring privacy and security of online conversations has gained paramount importance. Encrypted messaging apps have risen in popularity due to their commitment to safeguarding user data. However, the legal framework governing these platforms, particularly in relation to the FBI’s ability to access content and metadata, remains a topic of debate. Here, we delve into the landscape of secure messaging app accessibility, highlighting key points about various platforms and the extent to which they can be legally accessed.
Apple iMessage: Balancing Security and Accessibility
Apple’s iMessage is known for its end-to-end encryption, which means that only the sender and recipient can access the content of their conversations. However, certain legal measures can grant the FBI limited access.
The FBI can access limited message content from iMessage, such as the sender and recipient of a message, the date and time of the message, and the length of the message. The FBI can also access basic subscriber information, such as the name, phone number, and email address of the account holder.
The FBI can obtain this information with a subpoena, which is a court order that requires a person or organization to provide certain information. The FBI can also obtain this information with a search warrant, which is a court order that allows the FBI to search a person or place for evidence.
Line, Signal, and Telegram: Varied Degrees of Access
Line, Signal, and Telegram all provide varying levels of information to law enforcement. Line can offer registered information and limited text chats if end-to-end encryption is not applied. Signal, famous for its strong encryption, retains minimal data, including user registration and last connectivity date. Telegram lacks message content access but may disclose IP and phone numbers for confirmed terrorist investigations.
Threema and Viber: Privacy as a Priority
Threema and Viber prioritize user privacy, with no message content accessible. Threema provides hashed phone numbers and email addresses, along with other non-content-related data. Viber offers account registration and message history data but does not provide message content.
WeChat and WhatsApp: A Spectrum of Data Access
WeChat, primarily popular in China, has limitations in providing data for accounts created within the country. For non-China accounts, basic information is available, excluding message content. WhatsApp, while offering end-to-end encryption, can provide limited subscriber records through subpoenas. Court orders yield more comprehensive information, including address book contacts and blocked users. Search warrants enable access to address book contacts and pen register data, revealing source and destination of messages. iCloud returns can potentially contain WhatsApp data, including content, if iCloud backups are enabled.
Wickr: Transparency and Limited Access
The FBI cannot access any message content from Wickr. Wickr uses end-to-end encryption, which means that the messages are encrypted on the sender’s device and only decrypted on the recipient’s device. The FBI does not have the keys to decrypt the messages.
The FBI can only access basic subscriber information from Wickr, such as the date and time the account was created, the type of device(s) the app was installed on, and the date of last use. The FBI can obtain this information with a subpoena or a search warrant.
Wickr, known for its emphasis on security, maintains a relatively transparent approach. It offers minimal data, such as account creation date, device information, and the number of messages exchanged. However, message content and external IDs remain inaccessible.
It is important to note that the FBI’s ability to access secure messaging app data is constantly evolving. As new technologies are developed, the FBI may be able to access more data from these apps.
As the popularity of encrypted messaging apps grows, striking a balance between user privacy and national security remains an ongoing challenge. The FBI’s ability to access content and metadata from these platforms hinges on various legal measures, including subpoenas, court orders, and search warrants. Users must remain vigilant about the security measures these platforms employ and stay informed about their rights and the extent to which their data may be accessed under the law.
If you are concerned about your privacy, you should use a secure messaging app that does not store any data on its servers. This means that even if the FBI gets a warrant, they will not be able to access any of your messages. Some examples of secure messaging apps that do not store data on their servers include Signal and Threema.
It is also important to be aware of the risks associated with using any messaging app. Even if the app uses end-to-end encryption, there are still ways for law enforcement to get access to your messages. For example, if you are using a messaging app on a device that is not your own, the owner of the device may be able to access your messages. Additionally, if you are using a messaging app that is not popular, it may be more vulnerable to attack.
Ultimately, the best way to protect your privacy is to use a secure messaging app that you trust and to be aware of the risks involved.
Here are some additional tips for protecting your privacy when using secure messaging apps:
- Do not use the same password for all of your accounts.
- Enable two-factor authentication whenever possible.
- Be careful about what information you share in your messages.
- Keep your devices up to date with the latest security patches.
By following these tips, you can help to protect your privacy and keep your messages safe.
See also