End-to-end encryption introduction
Everything you should know about End-to-end encryption.
What is End-to-end encryption
End-to-end encryption (E2EE) is a system of communication where only the communicating users can read the messages. In principle, it prevents potential eavesdroppers – including telecom providers, Internet providers, and even the provider of the communication service – from being able to access the cryptographic keys needed to decrypt the conversation.
In many messaging systems, including email and many chat networks, messages pass through intermediaries and are stored by a third party, from which they are retrieved by the recipient. Even if the messages are encrypted, they are typically only encrypted ‘in transit’, and are stored in decrypted form by the third party. This allows the third party to provide search and other features, or to scan for illegal and unacceptable content, but also means they can be read and misused by anyone who has access to the stored messages on the third party system, whether this is by design or via a backdoor. This can be seen as a concern in many cases where privacy is very important, such as persons living under repressive governments, whistleblowing, mass surveillance, businesses whose reputation depends on its ability to protect third party data, negotiations and communications that are important enough to have a risk of targeted ‘hacking’, and where sensitive subjects such as health, and information about minors are involved.
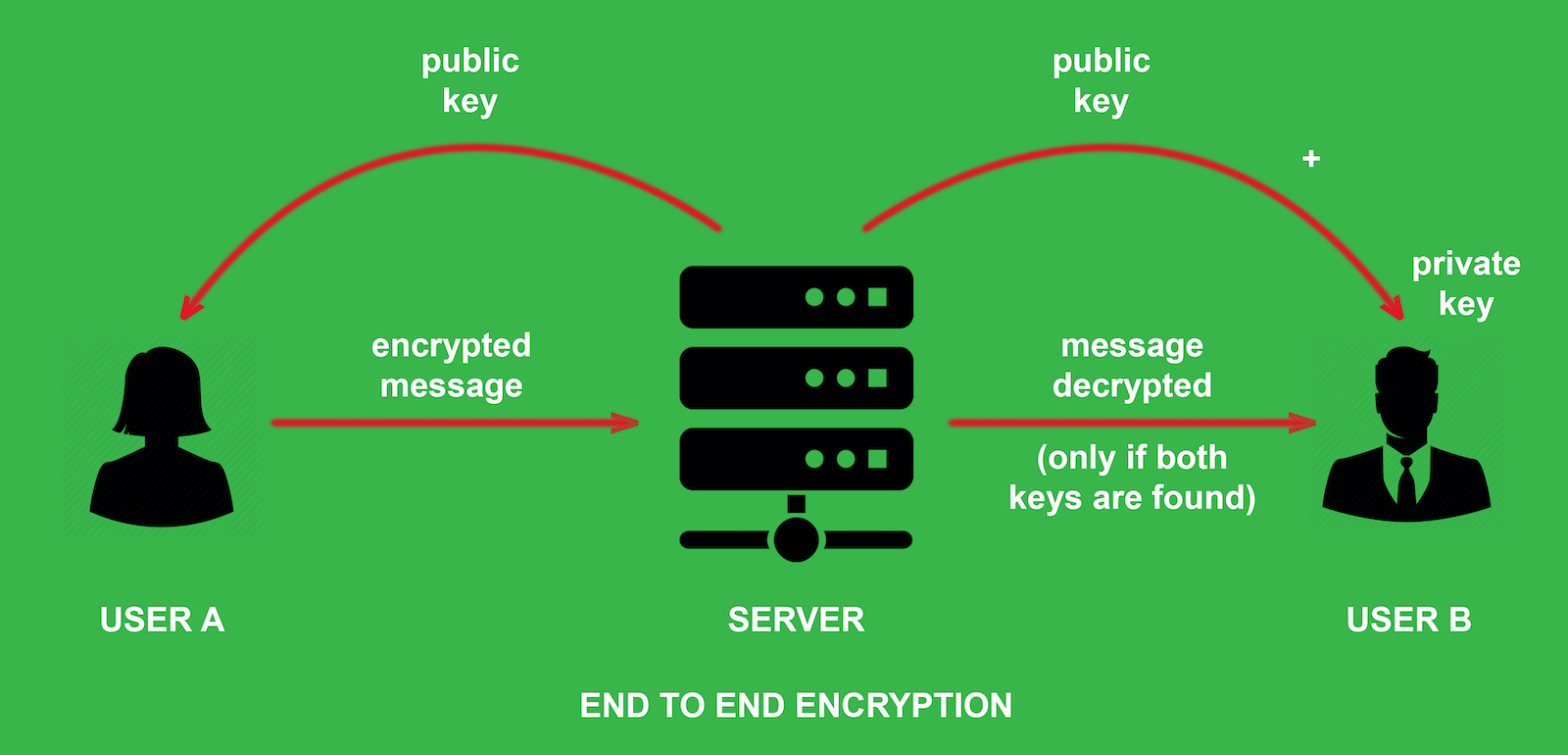
Why we need End-to-end encryption
To better protect your privacy.
End-to-end encryption is intended to prevent data being read or secretly modified, other than by the true sender and recipient(s). The messages are encrypted by the sender but the third party does not have a means to decrypt them, and stores them encrypted. The recipient retrieves the encrypted data and decrypts it themselves.
Because no third parties can decipher the data being communicated or stored, for example, companies that use end-to-end encryption are unable to hand over texts of their customers’ messages to the authorities
How
In an End-to-end encryption system, encryption keys must only be known to the communicating parties. To achieve this goal, E2EE systems can encrypt data using a pre-arranged string of symbols, called a pre-shared secret (PGP), or a one-time secret derived from such a pre-shared secret. They can also negotiate a secret key on the spot using Diffie-Hellman key exchange.
Standards
Signal Protocol
Signal Protocol provides confidentiality, integrity, authentication, participant consistency, destination validation, forward secrecy, post-compromise security (aka future secrecy), causality preservation, message unlinkability, message repudiation, participation repudiation, and asynchronicity.
The Signal Protocol also supports end-to-end encrypted group chats. The group chat protocol is a combination of a pairwise double ratchet and multi-cast encryption. In addition to the properties provided by the one-to-one protocol, the group chat protocol provides speaker consistency, out-of-order resilience, dropped message resilience, computational equality, trust equality, subgroup messaging, as well as contractible and expandable membership.
Apps use Signal Protocol
- Signal
- WhatsApp (2014)
- Facebook Messenger (2016)
- Skype (2018)
PGP
Pretty Good Privacy (PGP) is an open source encryption program used for signing, encryption.
Best Practices
- Always use encrypted communication channel like
https. - Use end to end encrypted enabled apps provide end to end encryption function.
- Full disk encryption to protect your local data.